Enjoy! Follow us for more...
HOW TO FIND ORIGIN SERVERS OF WEBSITES BEHIND BY CLOUDFLARE USING INTERNET-WIDE SCAN DATA FROM CENSYS
How to Find origin servers of websites behind by CloudFlare using Internet-wide scan data from Censys
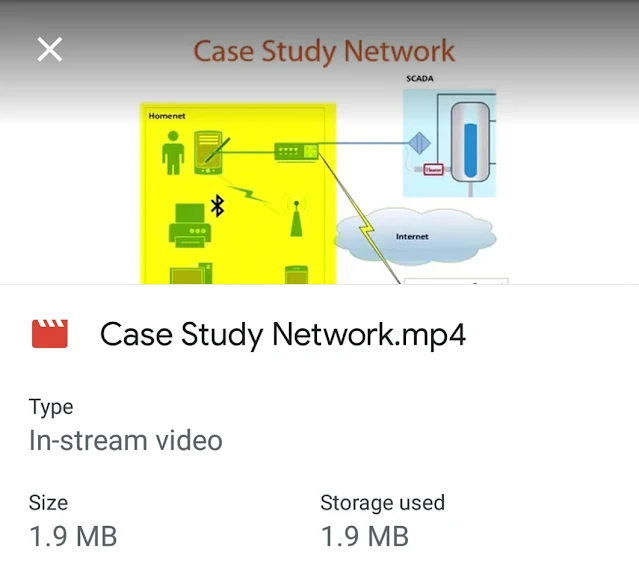
CloudFlair is a tool to find origin servers of websites protected by CloudFlare who are publicly exposed and don't restrict network access to the CloudFlare IP ranges as they should.
The tool uses Internet-wide scan data from Censys to find exposed IPv4 hosts presenting an SSL certificate associated with the target's domain name.
1) Register an account (free) on https://censys.io/register
2) Browse to https://censys.io/account/api, and set two environment variables with your API ID and API secret
3) export CENSYS_API_ID=...
4) export CENSYS_API_SECRET=...
5) Clone the repository
git clone https://github.com/christophetd/cloudflair.git
cd cloudflair
pip install -r requirements.txt
Run CloudFlair (see Usage below for more detail)
python cloudflair.py myvulnerable.site
Then
python cloudflair.py --help
usage: cloudflair.py [-h] [-o OUTPUT_FILE] [--censys-api-id CENSYS_API_ID]
[--censys-api-secret CENSYS_API_SECRET]
domain
Docker image
A lightweight Docker image of CloudFlair (christophetd/cloudflair) is provided. A scan can easily be instantiated using the following command.
1) docker run --rm -e CENSYS_API_ID=your-id -e CENSYS_API_SECRET=your-secret christophetd/cloudflair myvulnerable.site
2) You can also create a file containing the definition of the environment variables, and use the Docker--env-file option.
cat censys.env
CENSYS_API_ID=your-id
CENSYS_API_SECRET=your-secret
docker run --rm --env-file=censys.env christophetd/cloudflair myvulnerable.site
Follow us for more...
Search engines for data breach related queries.
https://intelx.io/
https://leaked.site/
https://ghostproject.fr/
https://www.dehashed.com/
https://leakedsource.ru/main/
https://joe.black/leakengine.html/
https://services.normshield.com/data-breach/
intelx.io (https://intelx.io/)
Intelligence X
Intelligence X is a search engine and data archive. Search Tor, I2P, data leaks and the public web by email, domain, IP, CIDR, Bitcoin address and more.
https://www.dehashed.com/
Dehashed includes different types of data like usernames, ip addresses, phone number, names and much more.
I haven't checked all of them so have a look at them.
It's just for general purpose (don't use them to harm anyone or include information collected from them in any illegal activity) I'm not blameworthy of anything done worng by you.
All the information present in above websites is open source.
~Invincianon
Enjoy! Follow us for more...
What is Double-testing with lookahead assertions in Regex.mp4
Download Video : What is Double-testing with lookahead assertions in Regex.mp4 Double-Testing with Lookahead Assertions (Regex) Double-te...

-
=========================== WHAT I'M ABOUT TO SHARE WITH YOU IS FOR EDUCATIONAL PURPOSES ONLY!!!I WILL NOT BE RESPONSIBLE FOR YOUR ACTI...
-
HOW TO UNBLOCK YOURSELF ON WHATSAPP IF SOMEONE BLOCKS YOU!! Step 1: Write down your blocker’s phone number If you have the contact that bloc...